I attended and gave a talk at the recent Irish Wireless Conf & Expo on behalf of INEX. I don’t get to do much with wireless links and as such I found many of the talks and exhibitors very interesting. One company that had a large presence through both Wireless Connect in Dublin and Irish Wireless in Shannon was Mikrotik – a company manufacturing routers built on Linux and some kit that I had been meaning to look at for some time.
Following the conference I picked up some RB750’s and RB750G’s and was very impressed. So much so, that I picked up a RB1100 also. The RB1100 specifications include:
- 13 individual 1Gbps ports;
- 2 x 5 port switch groups;
- 800MHz Power PC MPC8544E processor;
- SODIMM RAM slot with up to 1.5GB RAM;
- 1 x microSD card slot;
- 1U rack mount case.
I decided to benchmark this to see at just what rate it could route packets.
Benchmark Methodology and Tests
I used two PCs running Linux with iperf to measure TCP throughout with different packet sizes. To establish a baseline, I ran the same tests with the two PCs directly connected (this is the Direct Connection results below). The maximum achievable result with this is 1Gbps.
An example command line for the test which runs for 10 secs by default and for a packet size of 64 bytes is:
iperf -f m -i 1 -c 10.0.0.1 -l 64
Then I ran four test sets routing traffic between two networks as follows:
- No c/t, no f/w: connection tracking disabled and firewall set to allow all;
- No c/t, f/w: connection tracking disabled but with some simple firewall rules;
- C/t, no f/w: connection tracking enabled but firewall set to allow all;
- C/t, f/w: connection tracking enabled and stateful firewall rules.
In addition, I ran the above four tests with the RB1100 configured as a OpenVPN server:
/interface ovpn-server serverset auth=sha1,md5 certificate=cert1 \
cipher=blowfish128,aes128,aes192,aes256 \
default-profile=your_profile enabled=yes \
keepalive-timeout=disabled mac-address=FE:50:A7:D5:FE:B7 \
max-mtu=1500 mode=ip netmask=24 port=1194 \
require-client-certificate=no
One of the PCs was connected to the RB1100 as a VPN client pushing traffic to the other server on a non-VPN connect with all traffic routed through the RB1100. I also did a baseline test by running the VPN server with the same encryption on one of the PCs with a direct connect to the other and then pushing traffic over the VPN link.
Results:
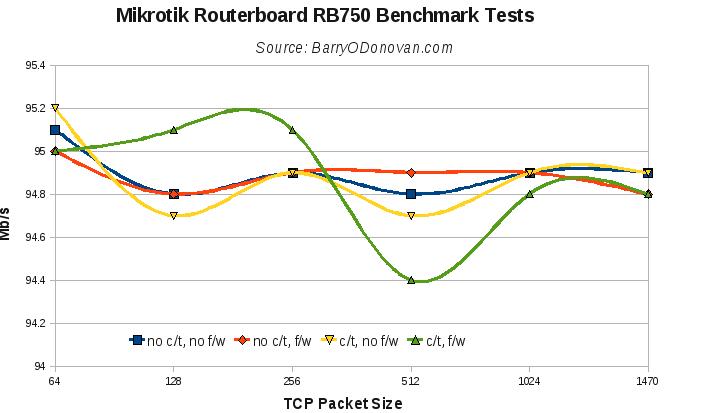
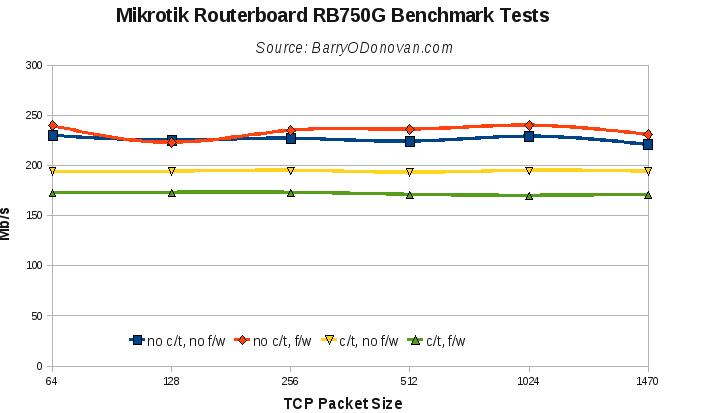
The results can be seen in the following graph:
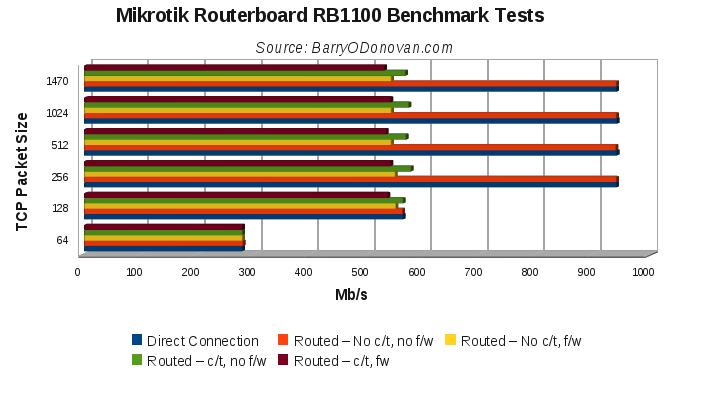
Without connection tracking and firewall, full line rate is achievable for packet sizes of 256bytes and higher – all in all, an excellent result. That said, no connection tracking and no firewall would be an unusual configuration and with these, the box maxes out at around 525Mbps – still an excellent result for less than €400.
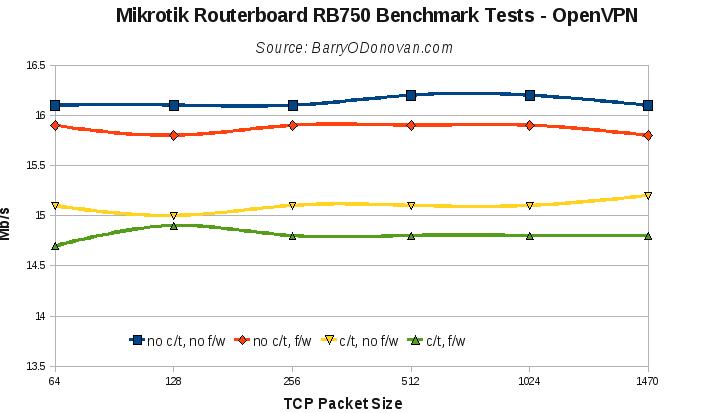
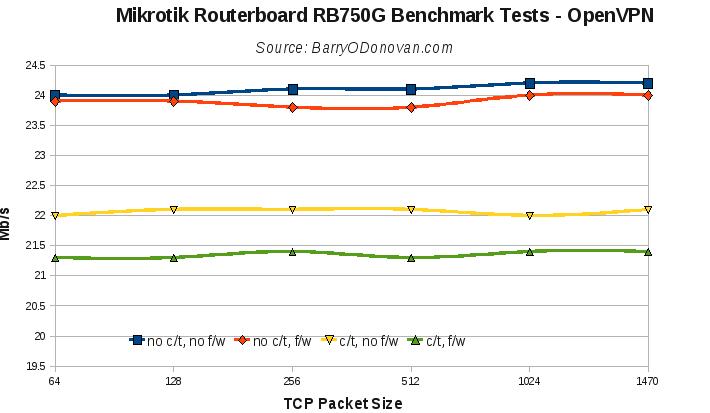
The VPN tests yielded:
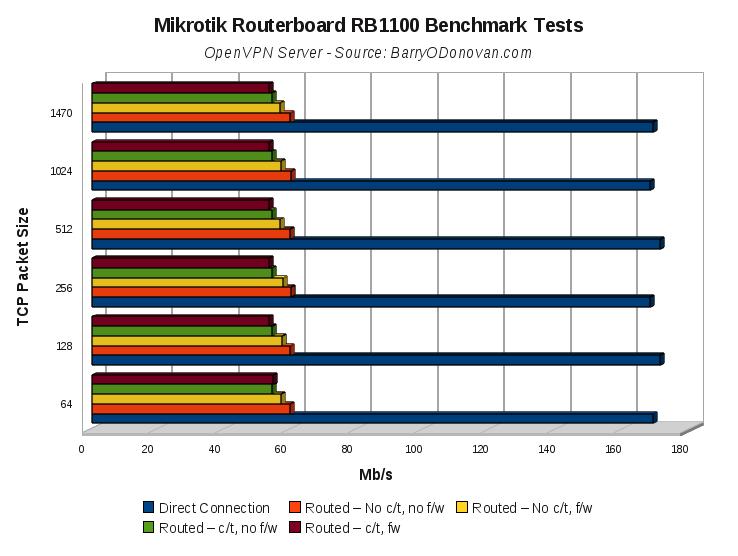 VPN throughput primarily relies on CPU horse power and the PCs used for the Direct Connection baseline test are pretty modern.
VPN throughput primarily relies on CPU horse power and the PCs used for the Direct Connection baseline test are pretty modern.