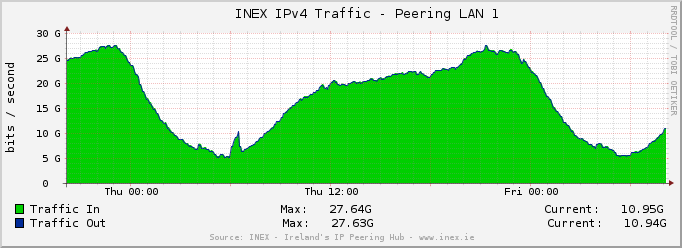
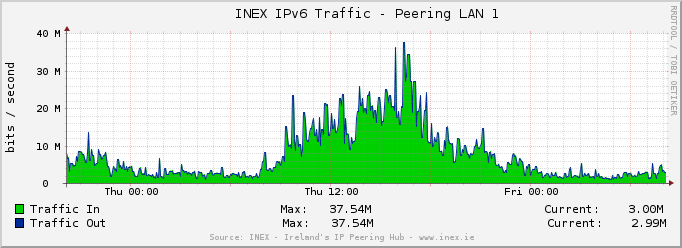
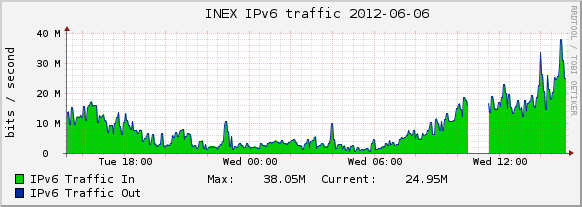
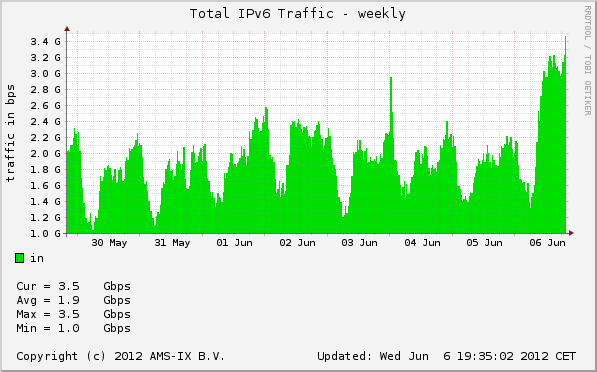
Over in INEX we run a route server cluster which alleviates the burden of setting up bilateral peering sessions for the more than 80% of the members that use them. The current hardware is now about six years old and we have a forklift upgrade in the works.
BGP allows for MD5 authentication between clients (using the TCP MD5 signature option, see RFC 2385) and – while recently obsoleted in RFC 5925 – it is still widely used in shared LAN mediums such as IXPs; primarily to prevent packet spoofing and session hijacking via recycled IP addresses.
Our current route server implementation runs on FreeBSD which does not support TCP MD5 in its stock kernel (you are required to compile a custom kernel – see below for details). Additionally, specifying the session MD5 is not done in the BGP daemon configuration but separately in the IPsec configuration. Lastly, our current FreeBSD version has no support for TCP MD5 Â over IPv6. These have all led to unnecessarily complex configurations and a degree of confusion.
Because of this, we decided to test up to date Linux and FreeBSD versions for native IPv4 and IPv6 TCP MD5 support with Bird and Quagga (our route server daemons of choice).
In each case, BGP sessions were tested for:
- no MD5 on each end (expected to work);
- same MD5 on each end (expected to work);
- different MD5 on each end (expected not to work); and
- MD5 on one end with no MD5 on the other end (expected not to work).
For Linux, the platform chosen was Ubuntu 12.04 LTS with the stock 3.2.0-40-generic kernel.
- Sessions were tested for Quagga to Quagga and Quagga to Bird;
- Sessions were tested over both IPv4 and IPv6;
- The presence of valid MD5 signatures were confirmed using
tcpdump -M xxx; - Stock Quagga and Bird from the 12.04 apt repositories were used.
The results -Â everything worked and worked as expected:
- BGP sessions only established when expected (no MD5 configured, same MD5 configured);
- This held for both IPv4 and IPv6.
Summary: Linux will support TCP MD5 nativily for IPv4 and IPv6 when using Quagga or Bird.
For FreeBSD, we used the latest production release of 9.1. TCP MD5 support is not compiled in by default so a custom kernel must be built with the additional options of:
options TCP_SIGNATURE options IPSEC device crypto device cryptodev
In addition to this, the MD5 shared secrets need to be added to the IPsec SA/SD database via the setkey utility or, preferably, via the /etc/ipsec.conf file which, for example, would contain entries for IPv4 and IPv6 addresses such as:
add 192.0.2.1 192.0.2.2 tcp 0x1000 -A tcp-md5 "supersecret1"; add 2001:db8::1 2001:db8::2Â tcp 0x1000 -A tcp-md5 "supersecret2";
where the addresses ending in .1/:1 are local and .2/:2 are the BGP neighbor addresses. This file can be processed by setting ipsec_enable="YES" in /etc/rc.conf and executing /etc/rc.d/ipsec reload.
- Sessions were tested for Quagga/Linux to Quagga/FreeBSD and  from Quagga/Linux to Bird/FreeBSD;
- Sessions were tested over both IPv4 and IPv6;
- The presence of valid MD5 signatures were confirmed usingÂ
tcpdump -M xxx; - Stock Quagga from the 12.04 apt repositories and stock Quagga and Bird from FreeBSD ports were used.
The results – almost everything worked and worked as expected:
- BGP sessions only established when expected (no MD5 configured, same MD5 configured);
- This held for both IPv4 and IPv6;
- one odd but expected behavior – you only need to set the MD5 via
setkey/ipsec.conf– setting it (or not) in the Quagga and Bird config has no effect so long as it is set viasetkey(but is useful for documentation purposes). However, trying to set it in Quagga without having rebuilt the kernel will result in an error.
Summary:Â FreeBSD will support TCP MD5 via a custom kernel and setkey / ipsec.conf for IPv4 and IPv6. Note that there is an additional complexity when changing or removing MD5 passwords as these need to be amended / deleted via setkey which can put an extra burden on automatic route server configuration generators.