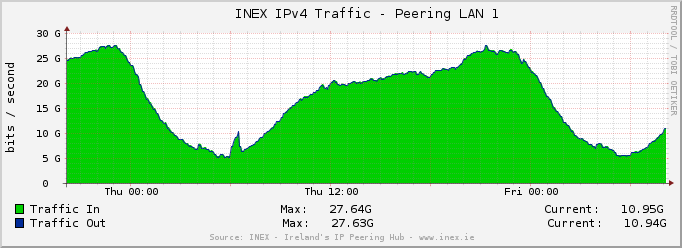
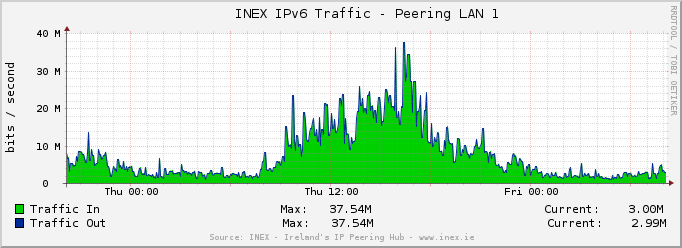
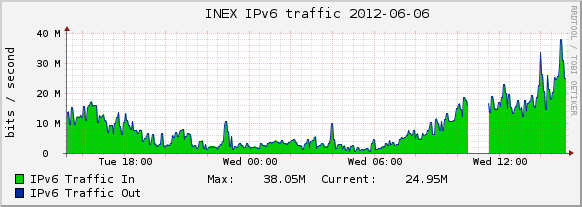
NOCtools is a mixed bag of tools and utilities that are useful for NOC engineers. This project originally started out as a way to highlight and utilise our OSS_SNMP library (a PHP SNMP library for people who hate SNMP).
It since grew into a way to graphically present information on network topology that is normally difficult and cumbersome to do by logging into individual devices. Such information includes a discovered L2 topology by CDP, using this to present rapid-PVST port roles and so forth.
From the company blog:
Today, we are introducing NOCtools which uses this library to provide a number of useful tools including:
- CDP Neighbours:Â for a given CDP enabled device, display its CDP neighbours with information and also a graph showing connected ports.
- CDP L2 Topology:Â graph the layer 2 network topology based on a recursive crawl of CDP neighbours.
- RSTP Topology & Port Roles: similar to CDP L2 Topology above but this takes a specific VLAN and identifies and graphs Per-VLAN Spanning Tree port roles.
- Per-VLAN RSTP Port Roles:Â a tool that will display the per-VLAN Rapid STP port roles for a given VLAN (or for all VLANs) on a device.
- Inter-Device VLAN Comparison:Â a tool that will compare VLANs available (and their respective names) across selected devices allowing you to ensure consistency as well as perform simple security audits.
Follow the links about for screen shots and more details. We are releasing this under a GNU GPL license in the hope that the wider networking community will benefit from them.