This article will describe my experiences in creating a read-only LDAP address book (with Thunderbird as a proof of concept); also known as a corporate directory. This is written by someone who has (to put it mildly) hated LDAP for years and dies a little every time he reads an introduction to LDAP that describes it in terms of DNS.
There is one important point to make before we start – while these instructions should apply to any *nix distribution, it uses OpenLDAP/slapd version 2.4 which uses the newer runtime dynamic configuration engine. All of the below performed on Ubuntu 12.10.
Installing OpenLDAP is as easy as (root user is assumed in all of the following):
apt-get install slapd ldap-utils
As part of this process, you’ll be asked to enter an admin password – record this as it will be stored in hashed format.
You can immediately run some LDAP queries to test / get to know your system:
- Dump your entire configuration:
ldapsearch -Y EXTERNAL -H ldapi:/// -b cn=config
- List all configuration objects:
ldapsearch -Q -LLL -Y EXTERNAL -H ldapi:/// -b cn=config dn
- List all installed schemas:
ldapsearch -Q -LLL -Y EXTERNAL -H ldapi:/// -b cn=schema,cn=config dn
In the output from the last command, you’ll see core, cosine, nis and inetorgperson. These are all we need for an address book directory. If you are so inclined, there is a published but neglected schema for Thunderbird specifically but it is not a standard and those fields may not (and probably will not) be supported by other clients.
One thing you might want to do before you start is up the logging level (from none by default) as follows. Don’t forget to change it back when you’re up and running as your logs will fill up fast.
cat <ldapmodify -Y EXTERNAL -H ldapi:///
dn: cn=config
changetype: modify
replace: olcLogLevel
olcLogLevel: 296
EOF
The installation will have created an organisation object based on your domain (or nodomain). E.g.
 ldapsearch -Q -LLL -Y EXTERNAL -H ldapi:/// -b dc=nodomain
dn: dc=nodomain
objectClass: top
objectClass: dcObject
objectClass: organization
o: nodomain
dc: nodomain
dn: cn=admin,dc=nodomain
objectClass: simpleSecurityObject
objectClass: organizationalRole
cn: admin
description: LDAP administrator
You can find out what domain yours is under by examining the olcSuffix field of the output of:
ldapsearch -Q -LLL -Y EXTERNAL -H ldapi:/// -b olcDatabase={1}hdb,cn=config
You may want to modify this to suit or add new objects. We’re going to add new objects – which will work fine as long as the new olcSuffix does not conflict with the output from the above.
Let’s start with creating a database for our directory. First we need a directory on the filesystem:
mkdir -p /var/lib/ldap/opensolutions
chown openldap: /var/lib/ldap/opensolutions
Now create a file (say db-create.ldif) with something like:
# Database creation
dn: olcDatabase=hdb,cn=config
objectClass: olcDatabaseConfig
objectClass: olcHdbConfig
olcDatabase: hdb
olcSuffix: dc=opensolutions,dc=ie
olcDbDirectory: /var/lib/ldap/opensolutions
olcRootDN: cn=admin,dc=opensolutions,dc=ie
olcRootPW: gOeBTo5vfBdUs
olcDbConfig: set_cachesize 0 2097152 0
olcDbConfig: set_lk_max_objects 1500
olcDbConfig: set_lk_max_locks 1500
olcDbConfig: set_lk_max_lockers 1500
olcDbIndex: cn,sn,uid,mail pres,eq,approx,sub
olcDbIndex: objectClass eq
olcLastMod: TRUE
olcDbCheckpoint: 512 30
olcAccess: to attrs=userPassword
by dn="cn=ldapadmin,dc=opensolutions,dc=ie" write
by anonymous auth
by self write
by * none
olcAccess: to attrs=shadowLastChange
by self write
by * read
olcAccess: to dn.base="" by * read
olcAccess: to *
by dn="cn=admin,dc=opensolutions,dc=ie" write
by * read
And instruct LDAP to create the database:
ldapadd -Y EXTERNAL -H ldapi:/// -f db-create.ldif
The above creates a new LDAP database with some useful indexes. You can ignore the olcAccess for now as we’ll come back and address this later. What is above is fairly typically of a default installation.
Now, we need to add an organization object, an admin user to manage that (i.e. add, edit and remove entries from the corporate database) and an organisationalUnit object to hold our staff information. Create a file (say opensolutions.ldif) containing:
# Organisation object
dn: dc=opensolutions,dc=ie
dc: opensolutions
description: Open Solutions Corporate Directory
objectClass: top
objectClass: dcObject
objectClass: organization
o: Open Source Solutions Limited
# Admin user
dn: cn=ldapadmin,dc=opensolutions,dc=ie
objectClass: simpleSecurityObject
objectClass: organizationalRole
cn: ldapadmin
description: Corporate Directory Administrator
userPassword: Jh90Ckb.c.Tp6
# Unit for our corporate directory
dn: ou=people,dc=opensolutions,dc=ie
ou: people
description: All people in Open Solutions
objectclass: organizationalUnit
And add these objects to the database:
ldapadd -x -D cn=admin,dc=opensolutions,dc=ie -W -f opensolutions.ldif
Note the password is as specified in the database creation object (ie. gOeBTo5vfBdUs in this case).
A quick work on security and access control. By default, anonymous users / anyone can read all your entries. If you are publishing a public directory, this may be okay. If not, create and auth.ldif file with (for example):
dn: olcDatabase={2}hdb,cn=config
changetype: modify
replace: olcAccess
olcAccess: {0}to attrs=userPassword,shadowLastChange
by dn="cn=ldapadmin,dc=opensolutions,dc=ie" write
by self read
by anonymous auth
by * none
olcAccess: {1}to dn.subtree="dc=opensolutions,dc=ie"
by dn="cn=ldapadmin,dc=opensolutions,dc=ie" write
by users read
And apply it with:
ldapmodify -Y EXTERNAL -H ldapi:/// -f auth.ldif
This will:
- allow access to user password fields for authentication purposes (not for reading);
- allow any authenticated user to read the corporate directory;
- allow the ldap admin to make changes;
- deny all other access to this database (implicit rule).
See OpenLDAP’s Access Control page for more information.
Now, let’s add two sample entries. Create a file people.ldif with:
dn: cn=Barry O'Donovan,ou=people,dc=opensolutions,dc=ie
objectClass: inetOrgPerson
uid: barryo
sn: O'Donovan
givenName: Barry
cn: Barry O'Donovan
cn: barry odonovan
displayName: Barry O'Donovan
userPassword: testpw123
mail: sample-email@opensolutions.ie
mail: sample-email@barryodonovan.com
o: Open Solutions
mobile: +353 86 123 456
title: Chief Packet Pusher
initials: BOD
carlicense: HISCAR 123
ou: Computer Services
dn: Joe Bloggs,ou=people,dc=opensolutions,dc=ie
objectClass: inetOrgPerson
uid: joeb
sn: Bloggs
givenName: Joe
cn: Joe Bloggs
displayName: Joe Bloggs
userPassword: testpw124
mail: joeb@opensolutions.ie
o: Open Solutions
title: Chief Coffee Maker
ou: Kitchen
Add these to the directory using the ldapadmin user:
ldapadd -x -D "cn=ldapadmin,dc=opensolutions,dc=ie" -w Jh90Ckb.c.Tp6 -f people.ldif
You can test this with a couple of searches:
ldapsearch -xLLL -D "cn=Barry O'Donovan,ou=people,dc=opensolutions,dc=ie" -w testpw123 \
-b dc=opensolutions,dc=ie
ldapsearch -xLLL -D "cn=Barry O'Donovan,ou=people,dc=opensolutions,dc=ie" -w testpw123 \
-b ou=people,dc=opensolutions,dc=ie mail=sample-email@opensolutions.ie
slapd will listen on all interfaces on the standard port (389) when installed on Ubuntu. So, to test, we turn to Thunderbird:
- Open the address book (e.g. Tools -> Address Book)
- Add a new directory (File -> New -> LDAP Directory…)
- In the General tab (assuming we’re setting up Barry O’Donovan’s Thunderbird), set:
Name: Corporate Directory (whatever you like)
Hostname: 127.0.0.1 (or as appropriate)
Base DN:Â ou=people,dc=opensolutions,dc=ie
Port number: 389
Bind DN:Â cn=Barry O’Donovan,ou=people,dc=opensolutions,dc=ie
- In the Advanced tab:
Don’t return more than 100 results – change if you wish
Scope: Subtree
Login method: Simple
- Click okay to save the settings
- Right click on the directory in the left pane and select Properties
- Test by going to the Offline tab and click Download Now
- Enter your password (and use the password manager) – password is as per the person object above and so in this case:Â testpw123
- Test by typing Joe into the search bar on the top right
- Joe Bloggs should appear in the results.
Congratulations! You have a corporate directory.
Next Steps
References
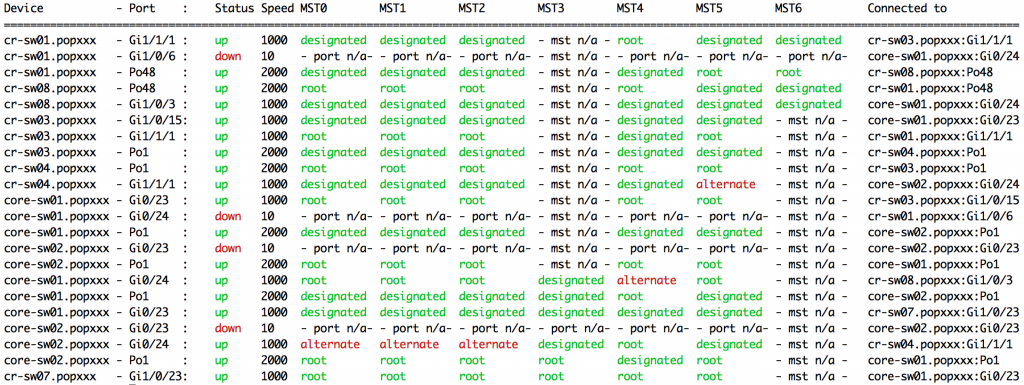 From a very simple array of port details at the top of the script, it will poll all switches and for each port print:
From a very simple array of port details at the top of the script, it will poll all switches and for each port print: